Credit image: Freepix
Top Ten Threats at a Glance
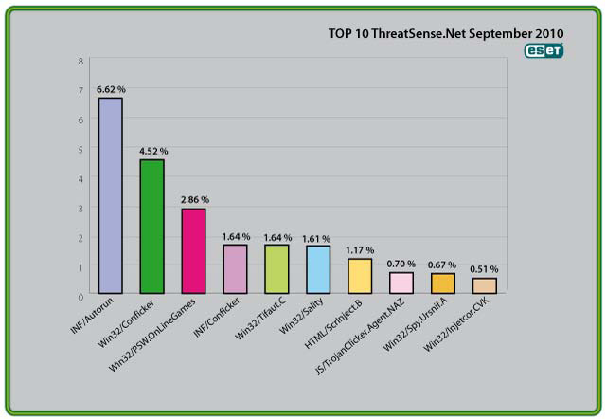
Analysis of ESET’s ThreatSense.Net®, a sophisticated malware reporting and tracking system, shows that the highest number of detections this month, with almost 6.62% of the total, was scored by the INF/Autorun class of threat.
1. INF/Autorun
Previous Ranking: 1
Percentage Detected: 6.62%
This detection label is used to describe a variety of malware using the file autorun.inf as a way of compromising a PC. This file contains information on programs meant to run automatically when removable media (often USB flash drives and similar devices) are accessed by a Windows PC user. ESET security software heuristically identifies malware that installs or modifies autorun.inf files as INF/Autorun unless it is identified as a member of a specific malware family.
Removable devices are useful and very popular: of course, malware authors are well aware of this, as INF/Autorun’s frequent return to the number one spot clearly indicates. Here’s why it’s a problem.
The default Autorun setting in Windows will automatically run a program listed in the autorun.inf file when you access many kinds of removable media. There are many types of malware that copy themselves to removable storage devices: while this isn’t always the program’s primary distribution mechanism, malware authors are always ready to build in a little extra “value” by including an additional infection technique.
While using this mechanism can make it easy to spot for a scanner that uses this heuristic, it’s better, as Randy Abrams has suggested in our blog (Threat Center) to disable the Autorun function by default, rather than to rely on antivirus to detect it in every case. You may find Randy’s blog at http://www.eset.com/threat-center/blog/2009/08/25/now-you-can-fix-autorun useful, too.
2. Win32/Conficker
Previous Ranking: 2
Percentage Detected: 4.52%
The Win32/Conficker threat is a network worm originally propagated by exploiting a recent vulnerability in the Windows operating system. This vulnerability is present in the RPC sub-system and can be remotely exploited by an attacker without valid user credentials. Depending on the variant, it may also spread via unsecured shared folders and by removable media, making use of the Autorun facility enabled at present by default in Windows (though not in Windows 7).
Win32/Conficker loads a DLL through the svchost process. This threat contacts web servers with pre-computed domain names to download additional malicious components. Fuller descriptions of Conficker variants are available at Conficker Page
While ESET has effective detection for Conficker, it’s important for end users to ensure that their systems are updated with the Microsoft patch, which has been available since the third quarter of 2008, so as to avoid other threats using the same vulnerability. Information on the vulnerability itself is available
3. Win32/PSW.OnLineGames
Previous Ranking: 3
Percentage Detected: 2.86%
This is a family of Trojans used in phishing attacks aimed specifically at game-players: this type of Trojan comes with keylogging and (sometimes) rootkit capabilities which gather information relating to online games and credentials for participating. Characteristically, the information is sent to a remote intruder’s PC.
These Trojans are still found in very high volumes, and game players need to remain alert. While there have always been unpleasant people who will steal another gamer’s credentials just for the heck of it, trading in virtual cash, treasure, avatars and so on is now a major source of illegal income for cybercriminals. It’s also important that participants in MMORPGs (Massively Multi-player Online Role Playing Games) like Lineage and World of Warcraft, as well as “metaverses” like Second Life, continue to be aware of the range of other threats like griefing ranged against them. The ESET Research team considered gaming malware in detail in the ESET 2008 Year End Global Threat Report, which can be found at PDF Report
4. INF/Conficker
Previous Ranking: 5
Percentage Detected: 1.64%
INF/Conficker is related to the INF/Autorun detection: the detection label is applied to a version of the file autorun.inf used to spread later variants of the Conficker worm.
As far as the end user is concerned, this malware provides one more good reason for disabling the Autorun facility: see the section on INF/Autorun above.
5. Win32/Tifaut.C
Previous Ranking: 4
Percentage Detected: 1.64%
The Tifaut malware is based on the Autoit scripting language. This malware spreads between computers by copying itself to removable storage devices and by creating an Autorun.inf file to start automatically. The autorun.inf file is generated with junk comments to make it harder to identify by security solutions. This malware was created to steal information from infected computers.
See INF/Autorun above for discussion of the implications of software that spreads using Autorun.inf as a vector.
6. Win32/Sality
Previous Ranking: 20
Percentage Detected: 1.61%
Sality is a polymorphic file infector. When run starts a service and create/delete registry keys related with security activities in the system and to ensure the start of malicious process each reboot of operating system. It modifies EXE and SCR files and disables services and process related to security solutions. More information relating to a specific signature:
W32 Sality Virus
7. HTML/ScrInject.B
Previous Ranking: 8
Percentage Detected: 1.17%
Generic detection of HTML web pages containing script obfuscated or iframe tags that that automatically redirect to the malware download. Malicious scripts and malicious iframes are a major cause of infection, and it’s a good idea to disable scripting by default where possible, not only in browsers but in PDF readers. NoScript is a useful open source extension for Firefox that allows selective disabling/enabling of Javascript and other potential attack vectors.
8. JS/TrojanClicker.Agent.NAZ
Previous Ranking: 7
Percentage Detected: 0.70%
This malware is a Trojan horse that does not generate copies of itself, but is usually part of other malware. It contains a list of web addresses to which to send requests, used to simulate clicking on advertisements for financial gain (click fraud).
9. Win32/Spy.Ursnif.A
Previous Ranking: 18
Percentage Detected: 0.67%
This label describes a spyware application that steals information from an infected PC and sends it to a remote location, creating a hidden user account in order to allow communication over Remote Desktop connections. More information about this malware is available at Win32/Spy.Ursnif.A
10. Win32/ Injector.CVK
Previous Ranking: n/a
Percentage Detected: 0.51%
Win32/Injector.CVK is the name for generic detection of malware that has capability to create and run a new thread with its own program code within a specific running process.